Data exposed include phone numbers, addresses and names of Covid-19 patients. Sensitive personal data has been improperly handled without the use of security protocols for over a month in a rush to design medical information platform by the Indian government.
22 Sep 2020

Ιndia has emerged as a hotspot for the Coronavirus pandemic, with the country witnessing around 100,000 cases daily.
Collating data of Coronavirus patients is the government’s responsibility, and it seems that the state government of Uttar Pradesh, the biggest state in India, has failed to safeguard the COVID-19 portal. As reported by security researchers from VPNMentor, the COVID-19 surveillance platform of Uttar Pradesh has been compromised, thus exposing the personal data of millions of Indians for anyone to access.
The platform, called “Surveillance Platform Uttar Pradesh Covid-19,”, reportedly built by the regional government of Uttar Pradesh, has numerous vulnerabilities that could jeopardize the country’s plans to control the spread of the virus.
First, the git repository used to store data of millions and contain the source code for the platform was unsecured. No security protocols were put in place, and anyone with knowledge of the platform’s URL and credentials of git repository could access the data.
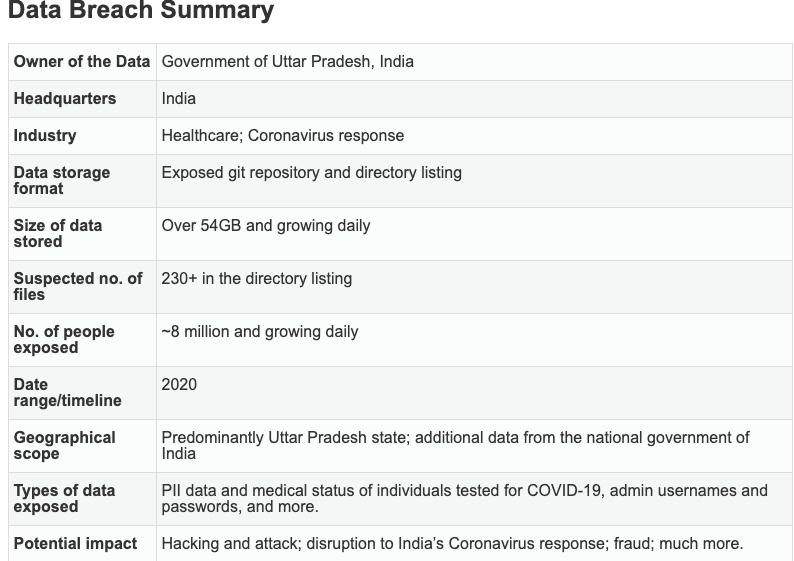
More importantly, the repository also had a data dump of the admin dashboard’s stored login credentials. The data dump included the username and password used to access the dashboard. Due to ethical reasons, the security researchers did not check manually using the exposed credentials to sign-in into the dashboard. However, through a thorough investigation, the team confirmed that the credentials were valid and could be used to access the dashboard.
Moreover, the admin passwords were four-digit numbers, and several accounts shared the same password, thus increasing the chances of illicit exposure if a hacker were to breach the portal.
Secondly, the researchers spotted a directory listing of CSV files in an exposed web index listing all the details of Coronavirus testing not only in Uttar Pradesh but in other parts of the country as well. These CSV files were available to the public without any password and had personally identifiable data of over 8 million people.
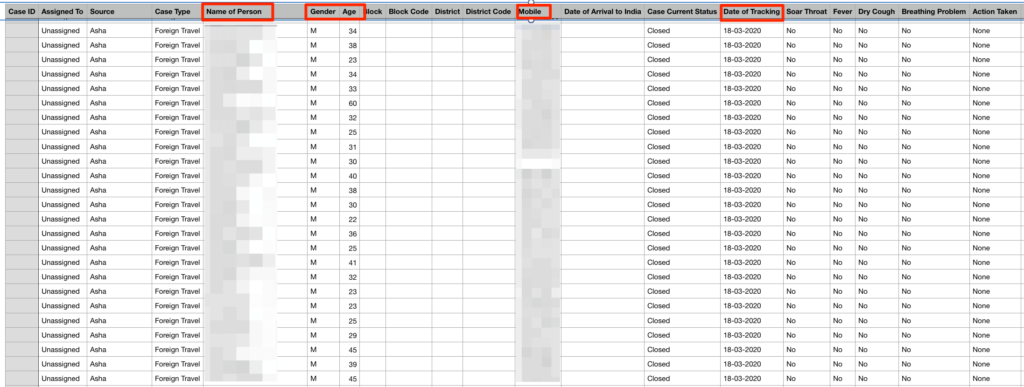
(Source: VPNMentor)
If a person with ill-intentions manages to access the dashboard, he could easily perform the following functions:
- Modify patient data
- Modify test results
- Send non-positive people to quarantine
- End quarantine period earlier than the designated date
- Switching the results of a Covid-19 negative patient with a positive patient, and vice versa
Security researchers have concluded that government officials overlooked several security protocols in a rush to develop a portal to track Coronavirus testing. It is still unclear whether anyone tried to access the exposed data, but the amount of data is colossal and, therefore, could fetch a reasonable sum of money if anyone grabs hold of it.
VPNMentor, along with The Next Web, contacted the UP government several times but failed to get a response. Considering the severity of the situation, they approached CERT-In, India’s threat response team. The data was finally secured on September 10 – almost a month after the Israeli embassy in India was first contacted by VPNMentor’s team.
(source)